“Agile security uses the methodology of agile software development to secure a continuous delivery pipeline. In this guide, we will answer the question “What is Agile Security?” and cover the need for agile security practices in a modern software development environment, as well as best practices for agile security. We will also take a look at agile application security platforms in more detail, and share the tools and technologies that can help businesses to deliver value faster without adding unnecessary risk.”
Agile application security is the way in which software development teams secure their agile ways of working and use core agile principles to shore up security. By leaning on agile across development and security too, they benefit from the velocity and flexibility of the agile methodology, without opening the business up to an unnecessary amount of risk.
Agile security, meaning how agile can work as a methodology for implementing security, is a popular topic, as an increasing number of enterprise businesses embrace the agile approach to ensure fast time to market and meet competitive demands. This guide will look at why agile security is necessary, and what tools, best practices, and mindset shifts are necessary to put it into practice and secure a continuous delivery pipeline.
What is Agile Security?
Agile development practices have transformed the way that applications are designed, built, tested and deployed. Instead of lengthy release cycles and rigid workflows, teams generally now work in iterative sprints, releasing new features and updates regularly and often continuously to allow them to react to customer demands and market needs. This agile way of working has accelerated innovation for development teams and allowed software companies to quickly and easily deliver value to their customers and users. However, it is not without its risks.
Agile security, meaning how teams secure the agile way of working and use the principles of agile for their own security approach has become a crucial practice that allows software companies to address agile application security challenges, improving on traditional security tools that were not created or adopted to manage environments with continuous code changes and a delivery pipeline which exists in constant motion. Instead of security being an afterthought which is tacked on right before deployment, agile application security allows security to become an integral and inherent part of the software development lifecycle (SDLC).
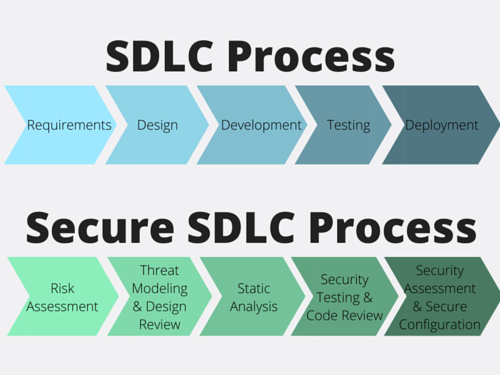
What Does an Agile Way of Working Look Like for Development Teams?
Agile development prioritizes flexibility and collaboration, putting the customer at the center of decision making, and using iterative development to work in short cycles and sprints to incrementally deliver value. Dev teams can quickly respond to user feedback, and iterate with adjustments and improvements in real time, rather than plan in a rigid way ahead of time.
In an agile workflow, you can expect to see frequent iterations with teams working in short cycles that are usually somewhere between two and four weeks. Updates are delivered incrementally, which means that teams can work with rapid feedback and regular adaptations.
It’s also common to see cross-functional teams in an agile working environment, with developers, product managers, operations stakeholders, designers, and security personnel all working together in a collaborative way to ensure faster decision making. Agile workflows use Continuous Integration and Continuous Delivery (CI/CD pipelines, accelerating release cycles by automating the process of integrating code changes and deploying them to production. In this way, teams can allow multiple updates per week or even multiple updates daily.
Agile working methodologies also tend to place a great amount of importance on customer and end-user feedback, so that teams can iterate based on real world experience rather than initial assumptions.
These core principles are often synonymous with agile environments, and allow software application teams to deliver value to their customers quickly and with great efficiency. However, as code is continually being modified, tested and deployed, it’s easier than ever for software vulnerabilities and misconfigurations to slip through the cracks. While traditional security practices are often designed for linear development models, agile requires something new.
What are the Security Challenges in Mind for Agile Application Security?
In a traditional more ‘waterfall’ method of working, security testing was usually added towards the end of the software development cycle. Today it’s common to hear organizations talking about a shift left approach — where security is placed earlier in the SDLC to identify vulnerabilities as early as possible, before they make it to production or become costlier to fix. This is because agile working methods open up specific security challenges, including:
- Regular code changes: In agile environments, developers are constantly pushing new code to repositories, often multiple times a day. Each code change, no matter how small, introduces a potential vulnerability. The high velocity of these changes increases the likelihood of security issues being introduced, especially when security checks aren’t embedded within each step of the pipeline. Without a robust security approach, agile teams risk deploying vulnerable code to production, potentially exposing users to breaches and data leaks.
- Speed Over Security: Agile is fundamentally about speed and flexibility. With pressure to release new features and improvements continuously, development teams may be incentivized to prioritize speed over security. Tight sprint deadlines can lead developers to bypass security checks or avoid them altogether, perceiving them as bottlenecks. This trade-off can be detrimental to the application’s overall security posture and, ultimately, the organization’s reputation and user trust.
- Limited Visibility and Control: Modern applications often rely on third-party libraries and open-source components to speed up development. While these dependencies offer valuable functionalities, they also introduce security risks, as vulnerabilities within a third-party library can provide attackers with a potential entry point. Agile development best practices can encourage developers to use libraries and third party components to meet project demands, and yes this can make it difficult for teams to keep track of every dependency and ensure each one is secure.
- Fragmented Ownership: In a traditional development environment, security might be handled by a dedicated team that performs periodic audits and testing. In agile environments, where cross-functional teams share responsibilities, security ownership can become unclear. With multiple stakeholders working on different aspects of the project, gaps in communication or accountability can result in security issues going unaddressed. This fragmentation requires a cultural shift where everyone, from developers to product managers, takes ownership of security.
- Developer adoption and engagement: In agile workflows, multiple developers often work on the same codebase simultaneously. Ensuring that every team member follows standardized secure coding practices becomes more challenging as the team scales. Inconsistent practices or misunderstandings about secure coding guidelines can lead to vulnerabilities, such as improper data handling, lack of input validation, or insecure authentication processes.
Agile Security Best Practices
To address these challenges, agile security integrates security practices early and continuously within the agile development process. Instead of treating security as a separate phase, agile security incorporates security measures throughout the SDLC, ensuring that vulnerabilities are identified and resolved in real-time. Principles that define agile application security include:
Security as Code
Agile security advocates for automating security checks within the CI/CD pipeline, allowing them to run alongside other tests and deployments. By treating security as code, teams can integrate security controls directly into the development pipeline, ensuring that code changes are evaluated for potential vulnerabilities before they reach production. Examples of “security as code” include static application security testing (SAST) and dynamic application security testing (DAST), which can be automated to scan for vulnerabilities during every build.
Shift Left and Shift Everywhere
In agile security, shifting security left doesn’t just mean performing security checks earlier but embedding security thinking into the earliest stages of development. By incorporating security into user stories and acceptance criteria, agile security ensures that security requirements are addressed from the start. A robust application security platform will allow you to use testing tools like SAST to shift left on application vulnerabilities and source code errors at the earliest possible stage and shift everywhere throughout the entire SDLC, from code-to-cloud.
Understanding Security Debt
In an agile working methodology, prioritization is based on the concept of “security debt”. That means that each security story is assigned a value and the tasks left undone are considered as accumulated debt. The value is normally assigned around the potential return on investment; e.g. which tasks can be handled at the lowest cost during the development cycle compared to their cost to fix following that cycle.
This prioritization may also contain a full examination of the system’s nature and the possible lines of attack that have been deemed most likely. These are clearly of a higher priority to fix than threats that only exist in potential. Once prioritization of security risks for agile security development has taken place, it’s a simple process to assign the related tasks to the individual team members. This allows each role (for example; testers, developers, and architects) to cover areas of their strengths and contribute to the agile security process.
Encourage Developers to be Security Champions
By empowering developers to take responsibility for security, organizations can foster a culture of security awareness that aligns with Agile’s collaborative nature and helps create a thriving DevSecOps culture. While your ultimate goal is to empower and engage all developers to make security part of their everyday work, agile security often involves designating specific security champions within development teams. These individuals serve as security advocates, helping their peers understand security best practices, ensuring compliance with security guidelines, and acting as liaisons between the development and security teams.
Continuous Monitoring and Real-Time Threat Detection
Traditional security assessments and audits are unlikely to be sufficient to secure agile environments, where code is deployed to production far more frequently. Agile security emphasizes continuous monitoring and real-time threat detection to identify and address vulnerabilities in real time. Implementing tools that continuously monitor the application for unusual activity, such as unauthorized access attempts or unusual data flows, allows agile teams to respond to threats quickly and proactively.
Threat Modeling and Risk-Based Testing
Agile security incorporates threat modeling and risk-based testing as regular parts of the development process. Threat modeling, where teams identify and assess potential risks early in the design phase, allows developers to anticipate threats before writing code. Risk-based testing prioritizes security alerts based on the severity and likelihood of specific vulnerabilities, ensuring that critical risks are prioritized and addressed first, using tools like guided remediation to speed up time to resolution. These practices allow agile teams to allocate security resources effectively without disrupting their workflow.
Using the Agile Methodology to Implement Agile Security
Considering these best practices, there is a clear connection between securing agile working methodologies, and the agile mindset itself. In that way, agile security is really an extension of agile development — incorporating security in an agile way so that the software development lifecycle and a continuous delivery pipeline can be secured.
To embrace agile security, think about how you can achieve minimal disturbance to the software development lifecycle, but obtain almost real-time results for mitigation. Just like any other agile project, security should focus on:
- Collaboration: Encourage communication between dev teams, security teams, operations teams, and any other stakeholders. Promote security as a shared responsibility rather than something that only security staff should be concerned by.
- Testing early and continuously: Testing applications is not a one-and-done task. Instead, teams should be able to automate security testing and integrate these into developer workflows for ease of access and use.
- Prioritizing based on risk: Ensure you have a method in place to uncover the most dangerous vulnerabilities according to business risk so that you can use resources wisely, and mitigate the most important issues quickly and effectively.
- Flexibility: Security should not be a rigid set of rules that are enforced across the business. Instead, teams should be able to iterate security needs based on feedback and user and market demands, so that it evolves alongside the risk level.
- Continuous improvement: Any agile environment should have a deep focus on learning and improvement. DevSecOps teams should be able to investigate and learn from security issues, continuously improving their processes and playbooks.
- Velocity: By embedding security into each step of the agile process, organizations can maintain a robust security posture without sacrificing the agility that modern software development demands.
The Building Blocks of Agile Application Security
Transitioning to an agile security mindset involves more than understanding wider agile best practices; it requires a robust set of tools and processes that enable teams to seamlessly integrate security into each phase of development. An agile security-focused organization treats security as an ongoing process rather than a one-time event, and to accomplish this, teams need tools that empower them to build secure software at speed. Let’s explore the essential tools and processes that foster an agile security culture and allow organizations to address security dynamically across all stages of development.
1. Adopting Application Testing Tools for Continuous Security
To ensure security is built into every step of the agile process, an organization must adopt an integrated suite of application security testing tools that align with agile workflows. Key testing methodologies include:
- Static Application Security Testing (SAST): SAST tools are deployed early in the development process, scanning source code for vulnerabilities as developers write it. By integrating SAST into the IDE or CI/CD pipeline, developers can catch security issues before code reaches production, preventing vulnerabilities from being introduced into the live environment.
- Dynamic Application Security Testing (DAST): DAST tools analyze the application in real-time, simulating attacks to uncover runtime vulnerabilities. Since DAST doesn’t rely on source code access, it tests the application from an external attacker’s perspective, identifying security gaps in the running application.
- API Security: API security allows you to eliminate the use of shadow and zombie APIs, and to mitigate API-specific risks as early as possible, such as inadequate authentication and authorization.
- Software Composition Analysis (SCA): Many applications today leverage open-source libraries, and SCA tools identify vulnerabilities in these dependencies. By scanning libraries used in the codebase, SCA tools help teams avoid introducing vulnerabilities through third-party code, which is especially critical in agile environments where dependencies are frequently updated.
Each of these tools plays a role in enabling continuous security, ensuring vulnerabilities are identified early and continuously as the application evolves. Integrated application security testing tools can be triggered automatically within the CI/CD pipeline, allowing teams to maintain security at each stage without disrupting their workflows.
2. Automation and CI/CD Integration
Agile development thrives on automation, and to foster an agile security culture, security processes must be automated wherever possible. By integrating security checks directly into the CI/CD pipeline and into the developers’ usual tools, teams can catch vulnerabilities immediately as code is committed, keeping up with Agile’s rapid pace without slowing down deployment.
Automation in agile security includes:
- Automated Vulnerability Scanning: Set up security scans to run automatically at each build or release stage. This includes SAST, DAST, and SCA scans, which should be configured to provide real-time feedback to developers as soon as vulnerabilities are detected.
- Auto and Guided Remediation: Developers shouldn’t need to be security experts in order to add security to the way they work. Where possible, developers should be guided to best-fix locations to make it easier for them to implement mitigation without needing input from security teams. In some cases, these mitigations may even be automated from end-to-end.
- Automated Compliance and Policy Checks: Automate compliance checks to ensure that every release complies with organizational or regulatory security policies. This is especially useful for organizations that need to adhere to strict industry regulations, as it reduces the manual burden of compliance verification.
- Environment-specific Security Tests: As code moves through development, staging, and production environments, automated security checks should be tailored to the environment’s specific risks and requirements.
Automation is key to ensuring security practices are consistently applied without delaying development. By embedding security into CI/CD pipelines and tools, agile teams can receive real-time feedback, empowering developers to address issues immediately, rather than waiting for a separate security review.
3. Threat Modeling and Prioritization
Agile teams need to be able to quickly and easily prioritize security measures based on the potential risks unique to their application. Identifying and categorizing risks early in the development cycle, enables teams to focus on the most critical areas, ensuring that security resources are effectively allocated.
In agile security, threat modeling and prioritization is an iterative process that takes place throughout development:
- Early-stage Threat Modeling: At the beginning of each sprint, teams should conduct threat modeling sessions to identify potential risks associated with new features. This early identification helps developers design with security in mind, reducing the likelihood of introducing vulnerabilities in subsequent sprints.
- Dynamic Threat Modeling During Development: As the application evolves, continuous threat modeling allows teams to adapt to new security requirements that emerge due to code changes or evolving attack vectors.
- Risk-based Testing: Once threats are identified, agile teams can perform risk-based testing, focusing on the most impactful security concerns first. This approach prioritizes testing areas with the highest potential impact, such as input handling, authentication, and authorization mechanisms, which are common targets for attackers.
- Prioritization of Alerts: Teams should be able to identify the vulnerabilities which equate to the greatest business impact and those which can be deprioritized without potential harm. While we would never suggest ignoring any alerts, prioritizing based on exploitability is a way to gain visibility into which vulnerabilities need immediate efforts when attention is being pulled in multiple directions.
Threat modeling and prioritization provide agile teams with a roadmap for security, ensuring that the most critical areas are tested first and frequently. This proactive approach also fosters a security-focused mindset, as developers begin thinking about security risks as they build.
4. Fostering a Security-First Mindset for Developers
Tools alone cannot build an agile security culture; organizations must also invest in training and advocacy to foster a security-first mindset, especially to get buy-in and engagement from developers. Agile security relies on every team member taking ownership of security, and training ensures developers have the knowledge they need to write secure code from the outset.
Key strategies for building a security-first mindset and culture include:
- Regular Security Training and Workshops: Offer training on secure coding practices, vulnerability mitigation, and evolving threat vectors. Training should be updated regularly to cover the latest security risks and trends, ensuring developers remain equipped to handle new challenges. At Checkmarx, we offer Codebashing — continuous training through customized learning paths that offer role and application-based knowledge.
- Security Champions: Appoint security champions within development teams who are responsible for promoting security best practices. Security champions serve as advocates for security, helping their peers understand security requirements and ensuring adherence to secure coding guidelines.
- Developer-friendly Tools: Make it easy for dev teams to embed security as part of their workflows by using application security tools that can be accessed directly from their Integrated Developer Environment (IDE), work with the languages they prefer to use, and integrate with the tools they know and love. Without developers needing to leave their regular working environment, you encourage adoption and make it simpler for them to embrace security as all part of a day’s work.
Investing in ongoing training and fostering a culture of security awareness empowers developers to consider security as a core part of their role. As developers become more knowledgeable and engaged with security, the entire organization benefits from a stronger, more proactive security posture.
Agile Security Starts with an Application Security Platform that Promotes Continuous, Collaborative Security
At Checkmarx, we know that building an agile security culture requires a combination of the right tools, processes, and cultural investments. With integrated application security testing tools, CI/CD security, centralized dashboards, and ongoing developer support and training, Checkmarx One allows organizations to weave security into the fabric of their agile development processes, creating resilient applications that are tested at the earliest stages of the SDLC, and then remain secure as they evolve.
With Checkmarx One, developers have everything they need to develop at speed and to embrace the velocity offered by a continuous delivery pipeline that’s also secure enough to put security teams’ minds at rest. Features such as automating critical security testing like SAST and DAST, and including robust SCA so that developers can embrace the use of third-party components and open-source software libraries help to foster a collaborative approach to security and promote DevSecOps trust across teams. In that way, Checkmarx One enables organizations to continuously innovate without compromising on security, privacy, and compliance.
Ultimately, agile security is about creating a secure development environment that keeps up with the demands of modern software development, delivering applications that are innovative and first-to-market, and secure from the first line of code to the cloud.
Want to see how it works for yourself? Speak to us about a demo of Checkmarx One