Summary
“ If you’ve asked yourself what is product security, or wondered how to prevent product security attacks, this article is a great start. We answer the question of what is product security engineering, dive into product security vs application security, and explain how Checkmarx application security platform provides a holistic view.”
Product security, meaning how organizations ensure that a product is designed, developed, and maintained securely covers a wide range of activities. From the processes used by developers during coding, to the policies of the wider organization for access, and the technologies that come together to safeguard the product and its users from vulnerabilities — product security is a huge topic.
For some people, application security is considered to be a narrow subset of product security, and while application security brings to mind secure code practices, product security zooms out and looks at a wider scope — namely the entire product lifecycle. This article takes a look at the idea of product security, and how teams can engineer a wide range of facets that make up product security through a strong application security platform.
What is Product Security Engineering?
You may hear product security known as product security engineering. Either way, product security takes a wide view of security across the product life cycle, focusing on uncovering and mitigating vulnerabilities from the earliest stages of design, through to development, implementation, and maintenance.

Security principles are implemented at every phase of the product life cycle — across software, hardware, and systems components. It is a product security engineers’ job to be certain that security is baked into the entire product, with skills covering risk management, threat assessment, secure development practices, and ongoing testing and monitoring.
For example, if a product security engineer is working in a medical device company, they will protect the build of the device itself, as well as associated patient data once the product is live.
For mobile applications, product security engineering will cover authentication for the app, the protection of user data, and secure protocols and processes to ensure the app is not at risk of reverse engineering or other tampering.
In an IoT device use case, product security engineers will take responsibility over communications with the cloud and additional devices, software updates, and also the hardware security of the device itself.
As product security engineers have a lot of different kinds of tasks to stay on top of, you can expect them to have skills including:
- Cybersecurity: Secure coding practices, threat modeling, risk assessment, and expertise in varied cybersecurity fields.
- Programming & Development: Familiarity with development tools, languages (e.g., Python, C, Java), and frameworks, especially those related to secure coding.
- Security Testing: Hands-on experience with security testing tools like static code analysis tools, penetration testing frameworks, and vulnerability scanners.
- Collaboration & Communication: The ability to work closely with product managers, software developers, hardware engineers, and legal/compliance teams, to name just a few.
What are Some of the Key Facets of Product Security?
When it comes to product security, there are a number of core elements that you would expect to be included within a robust organizational strategy. These functions and methodologies are a good starting point for teams who are looking to ensure they have a holistic product security approach.
Security by Design
From the earliest conversations around a product — is there a security leader with a seat at the table? Here, product security teams ensure that security is baked into the architecture and design, including threat modeling to identify potential risks and vulnerabilities, and spot any weaknesses before they get any further. What impact will these risks have if left unchecked, and how can the team design mitigations or implement defenses to be proactive about risk management? Another element to consider is compliance, as products will have strict regulatory requirements they need to keep to in the markets where they are used.
At this stage, product security stakeholders might want to discuss specific compliance requirements, or more general best practices such as the principle of least privilege, or secure coding practices, so that the product development team are all on the same page.
A Secure Development Lifecycle
Adding security as early as possible in the software development lifecycle (SDLC) means that time and resources needed to solve vulnerabilities and fix problems can be minimized, as it’s always less work to fix something earlier in the cycle. Here, product security teams integrate security measures as early as possible, with a ‘shift left’ approach. This includes implementing secure coding practices, offering automated security testing such as SAST and DAST, and reviewing code and third party components for vulnerabilities using tools like SCA. Remember, testing shouldn’t stop when a product goes live, organizations also need post-production scanning and testing to ensure ongoing validation.
A big part of ensuring a secure development lifecycle is getting developers engaged and on board with security as part of their daily work. To help with this, application security platforms can offer automated security tools integrated into the IDE, so that developers don’t have to leave their tools or environment to implement fixes.
Vulnerability Management and Incident Response
Product security teams should always be actively looking for, identifying and addressing vulnerabilities, both in the software side of a product, and the hardware where necessary. A large part of this is designing systems that monitor the product’s security in real-time and identify anomalous or unusual behaviors. As there can be a deluge of information from monitoring tools, it’s important to have a process in place for prioritizing alerts and minimizing false positives, understanding where to best place efforts to see the greatest impact in risk reduction.
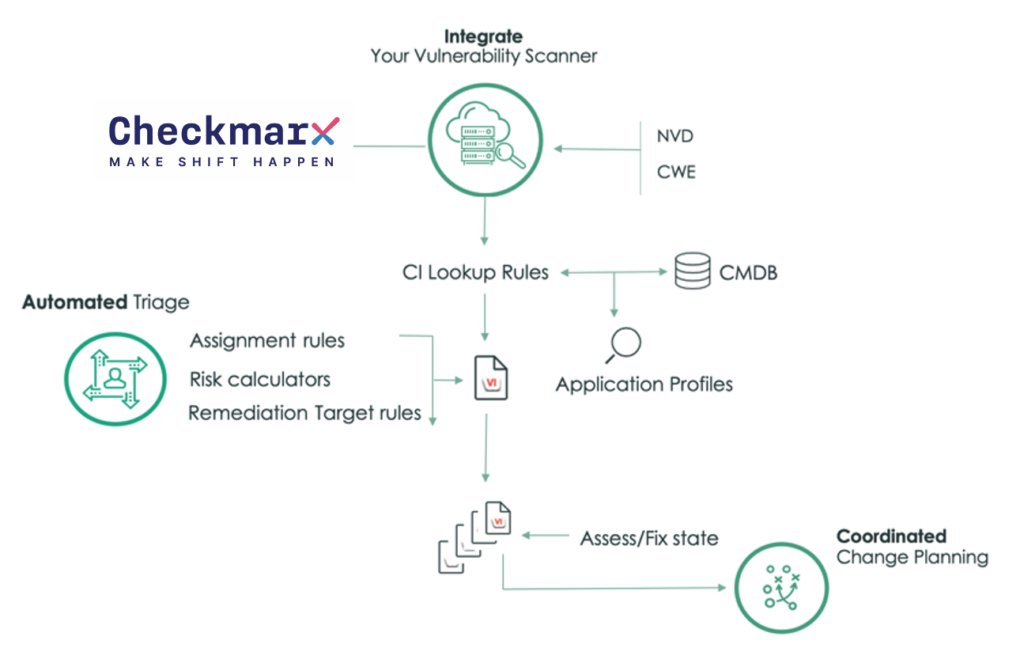
Security teams should work alongside developers to fix vulnerabilities, issue security patches, and release the right updates at the right time. In the case of an active threat, product security teams are also responsible for the incident playbook, establishing the procedures to support rapid response and recovery.
Supply Chain Security
Today’s developers rely heavily on third party libraries and components in order to improve development velocity and reduce rework. But these third party services can also open the product up to unnecessary risk.
Rather than stop developers from utilizing these sources, product security engineers can manage the associated risk by conducting due diligence on third party vendors, registries, libraries and services.
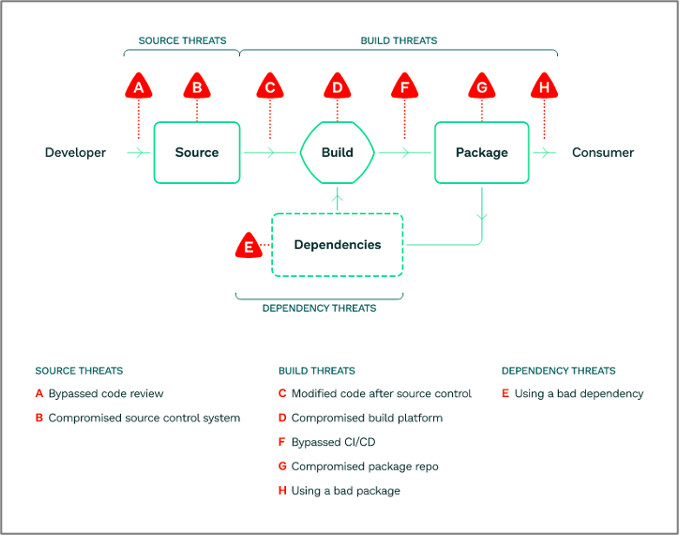
In some cases, they can also offer developers the right integrated tools to scan third party components and open-source software packages themselves to ensure that they do not contain any malicious code.
User and Data Privacy
Data is a powerful and in-demand commodity on today’s black market, so protecting user data is a crucial part of product security. Teams need to ensure data is protected both at rest, in transit, and during processing, and design products with data privacy at the core, for example using Privacy By Design best practices, or considering compliance laws like GDPR or CCPA.
In some cases, you may need product security engineers that can implement cryptographic measures, to protect sensitive data and secure communications. This could include specialties such as implementing data encryption processes or digital signatures for example.
Product Security vs Application Security
If you’ve always wondered about product security vs application security, that’s probably because they are pretty similar areas of the security world. While product security usually focuses on a broader scope, looking at the product from design through to maintenance, some would say application security is only about securing the application itself. In this way, while product security teams consider physical security, hardware and firmware as well as software, compliance, and incident response for the product — application security zooms into identifying and mitigating vulnerabilities in the application code, preventing attack types such as SQL injection and buffer overflows for example, and looking at app-specific vulnerability management, such as the list published by OWASP Top 10.
Application Security vs Product Security
| Product Security | Application Security | |
| Scope | Entire product lifecycle (hardware, software, systems) | Focuses on securing the software application itself |
| Focus | Holistic security, including hardware and supply chain | Specific to software code and logic |
| Components | Hardware, software, systems, network, supply chain | Secure coding, vulnerability management, app security |
| Responsibility | Cross-functional (hardware, software, legal, etc.) | Development and software security teams |
| Examples | A secure smartphone product or IoT device | A web or mobile application’s code and functionality |
| Tools | Threat modeling, supply chain security, device encryption | SAST, IaC security, SCA, DAST |
How to Prevent Product Security Attacks
As product security covers everything from design and development, to deployment and maintenance, a product security attack can cover a wide range of threats. However, there are certain best practices that can help organizations to ward off product security attacks, which lean on multi-layered security by design, proactive monitoring, and regular testing and updates. Think about:
- Security by Design: Ensure security is a fundamental consideration at the point of design, not tacked on after a product is ready for release. Conduct threat modeling early in the life cycle to uncover vulnerabilities, and encourage developers to follow secure coding principles — as outlined by your team for your specific business context.
- Comprehensive testing: Test, test, test — this is a crucial aspect of a secure application security environment. Use Static Application Security Testing (SAST) to find vulnerabilities in source code, and then Dynamic Application Security Testing (DAST) for runtime security, too. Make sure you automate testing where possible so you aren’t reliant on manual code reviews, as well as offering tools for manual scanning to identify complex vulnerabilities.
- Patch management: Implement a strong vulnerability management process which allows for prioritization, patching and then deployment of fixes. Set up automated and secure processes for delivering patches and updates to customers, and define how products will be maintained and secured after release, all the way to end-of-life.
- Authentication: This is an area for which many organizations fail to implement strong enough controls. Require MFA for users and administrators to access back-end systems. Implement Role-based Access Control (RBAC) with the principle of least privilege, so that users only have the minimum permissions they need to perform their daily work. Enforce strong password policies, with rules for rotation and complexity.
- Supply chain security: No application is an island. Many products rely on third-party sources, libraries and components, so implement a process for due diligence or testing inside the development workflow. Maintain a detailed Software Bill Of Materials (SBOM) which tracks all third-party components. If you’re partnering with third party vendors, implement a thorough risk assessment so that you know you’re not introducing risks to your own environment or product.
- Encourage DevSecOps practices: When teams work cohesively as one, security becomes part of the development process, rather than a frustration or a hurdle to velocity. Integrate security checks and scanning into CI/CD pipelines, and automate security tasks like code scanning so that issues are uncovered as early and continuously as possible. Even better if you can implement automated or integrated processes for container and IaC security, too, to automatically detect misconfigurations in cloud environments.
- Get developers on board: Training non-security teams is a tough battle, as development teams and engineers have their own busy workload. By implementing tools that are already part of their IDE out-of-the-box, it can reduce the friction for development teams, and encourage them to adopt secure coding practices and take autonomy over implementing security continuously as part of their work. This is crucial for maintaining a security-aware culture across the business.
Checkmarx Application Security Testing as Part of Product Security
Checkmarx One includes everything you need to secure your application from code to cloud. As part of a holistic product security strategy, Checkmarx takes a wider view, incorporating secure coding practices and application security testing including SAST, API security and DAST, as well as supply chain security such as Software Composition Analysis (SCA), malicious package protection and SBOM, and container security and IaC security on the cloud. Secure coding tools are incorporated into the developer workflow, and integrated into the IDE to make it easy to encourage a DevSecOps culture for the whole organization.
Application Security Risk Management with Checkmarx One
Checkmarx One
Application Security Risk Management
Application development is evolving with a shift towards cloud-native, the proliferation of open source, use of APIs, and AI-generated code. Security controls are needed at multiple points across the software development lifecycle. And all this requires more resources.
Checkmarx One comprehensive Risk Management feature that allows you to prioritize and understand the risks associated with your applications. Consolidate results from multiple scanners, and gain valuable insights and resources for team managers, especially AppSec teams.
More than simply application security alone, Checkmarx One helps you incorporate more of your product security necessities, all from a single platform so that you can see much faster time to value.
Ready to implement a strong application-centric product security solution? Speak to us about a demo of Checkmarx One.